Host your own VPN with WireGuard

You might have already heard of Virtual Private Networks or short VPNs. This is a technology that allows us to disguise our IP address while being online. We can just connect to a VPN server and from now on the websites we visit will only see the IP address of the VPN server instead of our own. There are some other advantages which we will further discuss in this blog post. So stay curious and happy reading.
How does a VPN work?
On a high level it is quite easy to understand. You can think of a VPN as a good man in the middle. Instead of connecting directly to the website you first establish a connection to your VPN server. You can then continue surfing while keeping your identity hidden. This is because the final website will not know who is using the VPN server it just sees that the server is making requests for somebody. Although, the VPN server of course knows your identity!
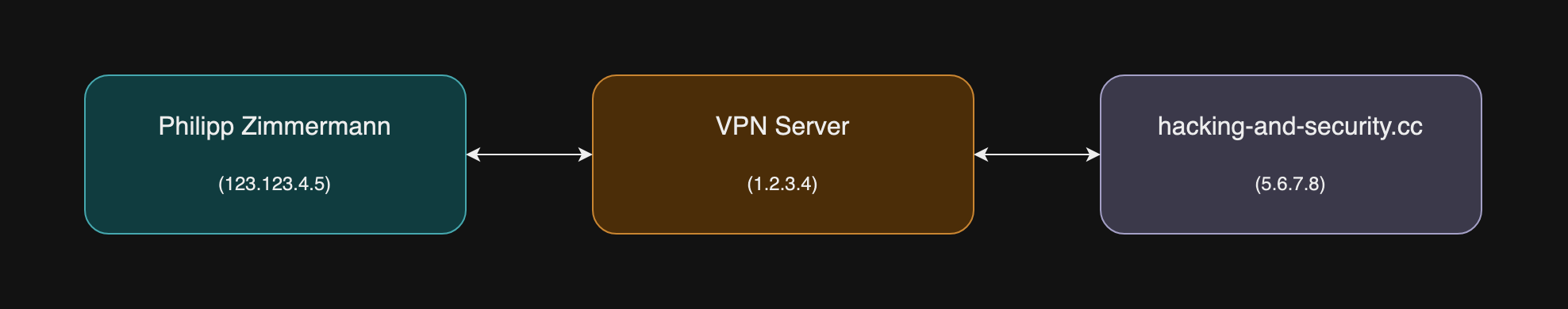
The visualization above shows me with my IP address of 123.123.4.5. Without a VPN the website I visit knows my IP address and therefore where I live, who my ISP is and even more sensitive information about me. Of course we do not want to give away all these kind of information like that. That's why I use the VPN. Now, when I connect to the website again the server sees the IP address of the VPN server (1.2.3.4) and has no idea who the initial sender was.
Advantages of using a VPN
As already mentioned a VPN is great for hiding your identity to services on the internet, but there are some other advantages.
- Bypassing geo-location restrictions - It's not a secret that websites adjust their content based on the location of their customers. An easy example would be streaming services like Netflix or Amazon Prime Video. But also other websites like News sites or blogs which are only accessible for users in a specific region. To bypass this restriction we can connect to a VPN in that specific country and we're good to go. Let's assume we want to watch a Netflix series that is not yet published in our country. We know that americans can watch it so we connect to a VPN server that is located in the United States. To Netflix it now looks like we were located in the United States and thus providing us our series.
- Traffic encryption - Do you know what an ISP is? It's your Internet Service Provider. The guys who provide you access to the internet. Of course you are paying for that service, but your money is not the only thing they collect. Your ISP is monitoring your network activities! Each router connection has its own IP address and thus can be identified. But what does that mean? Well, that means that your ISP knows who is paying for the service so they know your name, adress and your paying information of course. That's common knowledge I think. But, since they are routing all your traffic they know exactly which websites you visit. They also know when you visited them and for how long. They know your favourite restaurant, your e-mail provider, your goto search engine, anything. They collect and know everything you do online.
What your ISP knows about you:
- Name
- Adress
- Paying Information
- Visited Websites
- Timestamps of website visits
- Metadata (favourite restaurant, etc.)
I don't think I need to explain why we do not want us to be exposed like that. But I can explain how a VPN can help us in this case. As said before we always connect to the VPN before we visit a website. That means the only information our ISP gets is the IP address of our VPN server because we connect to it. So from the ISPs point of view we only visit one single website (our VPN). On top of that all traffic between you and your VPN is encrypted. So our ISP has no idea which websites we want the VPN to visit for us.
Another key aspect of traffic encryption is that you now can connect to public Wifi whithout being concerned anymore. The problem with public Wifi in public areas like airports, Starbucks or Libraries is that most of the time this Wifi is not encrypted. That means that when you are connected to such a network anybody who intercepts the traffic can read it. To be fair, if you're using "https"-connections the content is still encrypted but an adversary can still engineer the same information as your ISP. With a VPN however, this is not possible anymore. - Bypass censorship - Unfortunately not every country want's their citizens to have full access to the internet and therefore restricting it. This is possible by blocking websites that e.g. do not correspond to the desired political values. Again, a VPN can help in such situations because of the same reasons we discussed earlier. However, some countries also just block common VPN providers, which can make it a bit harder. So let's host our own!
Host your own VPN server
Why would we want to have our own VPN server? Well, first of all it's super cool. However, for me the main reason is the "No-Log-Policy". Many VPN providers tell us that they do not keep logs but of course we can never know for sure. So to ensure this we need to have our own instance where we have full controll over our data.
To do so, we will setup our own WireGuard instance using Docker Compose. We use WireGuard because it's state of the art, super fast and very easy to deploy.
First we need to check for the required packages. If docker is not installed already we can use the official installation guide to do so. Then we check the installation with the following commands.
# Check for docker
docker -v
# Check for docker compose
docker compose versionNow we need to create a new directory where we can save the docker-compose.yaml file to.
# Create a new directory
mkdir wireguard
# Change directory
cd wireguardNext step, we copy the following content to a file named docker-compose.yaml.
version: "2.1"
volumes:
config:
services:
server:
image: lscr.io/linuxserver/wireguard:latest
cap_add:
- NET_ADMIN
environment:
- PUID=1000
- PGID=1000
- TZ=Etc/UTC
- SERVERPORT=51820 # optional
- PEERS=2 # optional
- INTERNAL_SUBNET=10.10.10.0 # optional
- ALLOWEDIPS=0.0.0.0/0 # optional
- LOG_CONFS=true # optional
volumes:
- config:/config
ports:
- 51820:51820/udp
sysctls:
- net.ipv4.conf.all.src_valid_mark=1
restart: alwaysMost of the environment variables are self-explanatory. However if we want to dive deeper into the configuration here is their Github page.
The last todo is to start the container. We use the following command in the same directory where our docker-compose.yaml file is located.
# Start the stack and view the logs
docker compose up -d && docker logs -f wireguard-server-1If we did not change the LOG_CONFS environment parameter in the .yaml file we will see two QR-codes in our terminal (PEERS=2). These are the configurations that can be scaned with our WireGuard App on an iPhone or Android device.
To use our WireGuard instance on a computer we can copy the configuration files from the docker container to our host system like this:
# Copy configuration file and qr-code of peer1
docker cp wireguard-server-1:/config/peer1/peer1.conf ./
docker cp wireguard-server-1:/config/peer1/peer1.png ./
# Copy configuration file and qr-code of peer2
docker cp wireguard-server-1:/config/peer2/peer2.conf ./
docker cp wireguard-server-1:/config/peer2/peer2.png ./We can then download the files from our server to our local machine and we're good to go. Congratulations!



